The rapid shift to remote work has significantly impacted cybersecurity, creating new risks and vulnerabilities for businesses of all sizes. While the flexibility of remote work offers numerous benefits, it also brings challenges, particularly regarding data security. In this report, we’ll explore best practices for securing distributed teams, supported by industry research, case studies, and relevant data.
Current State of Cybersecurity in Remote Work EnvironmentsWith the rise of remote work, organizations have had to reconsider their cybersecurity strategies. This section highlights the most critical statistics and trends related to cybersecurity in remote work settings.
Key Statisticsshifted to remote work during the pandemic, and many continue to operate remotely or in hybrid environments.
report an increase in cyberattacks as a direct result of remote work.
surveyed in a 2023 report from PwC indicated they experienced security incidents in remote work settings.
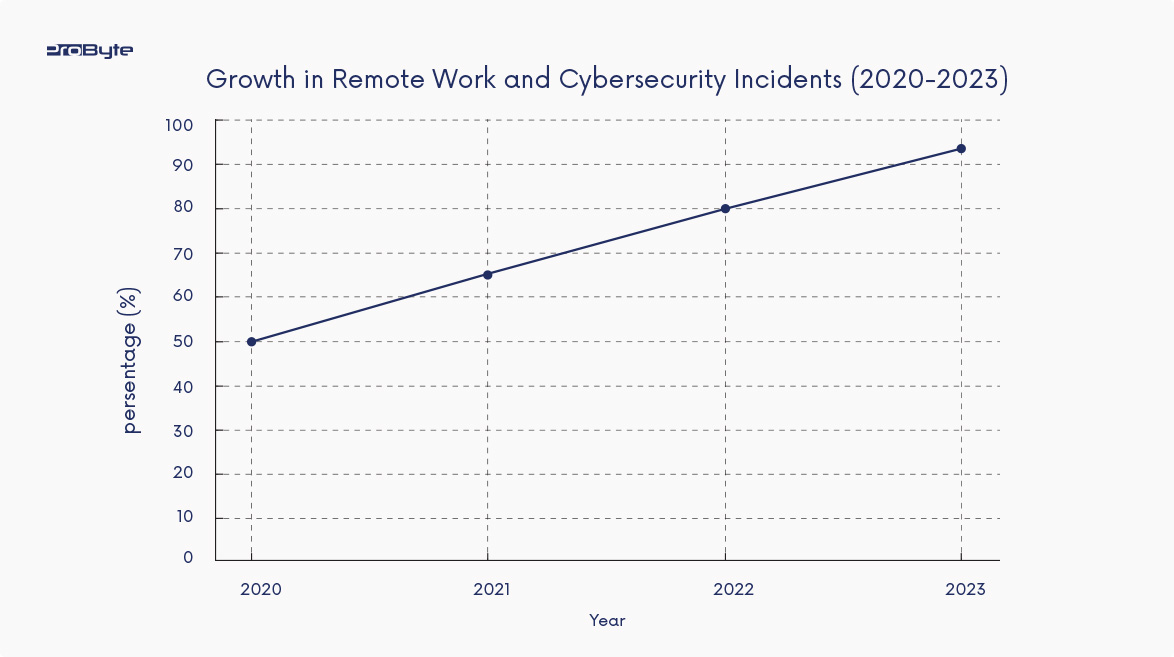 This graph highlights the significant increase in cybersecurity incidents as remote work became the norm.
This graph highlights the significant increase in cybersecurity incidents as remote work became the norm.
Remote work exposes organizations to a variety of cybersecurity risks. The following challenges must be addressed to ensure the security of distributed teams:
Many remote employees rely on weak or reused passwords, increasing the risk of account compromise.
With the shift to remote work, employees are more susceptible to phishing, vishing (voice phishing), and other forms of social engineering.
Remote workers often use personal devices and unsecured Wi-Fi networks, which are easier to exploit by cybercriminals.
Remote teams are often inadequately trained to recognize phishing attempts, ransomware attacks, and other cybersecurity threats.
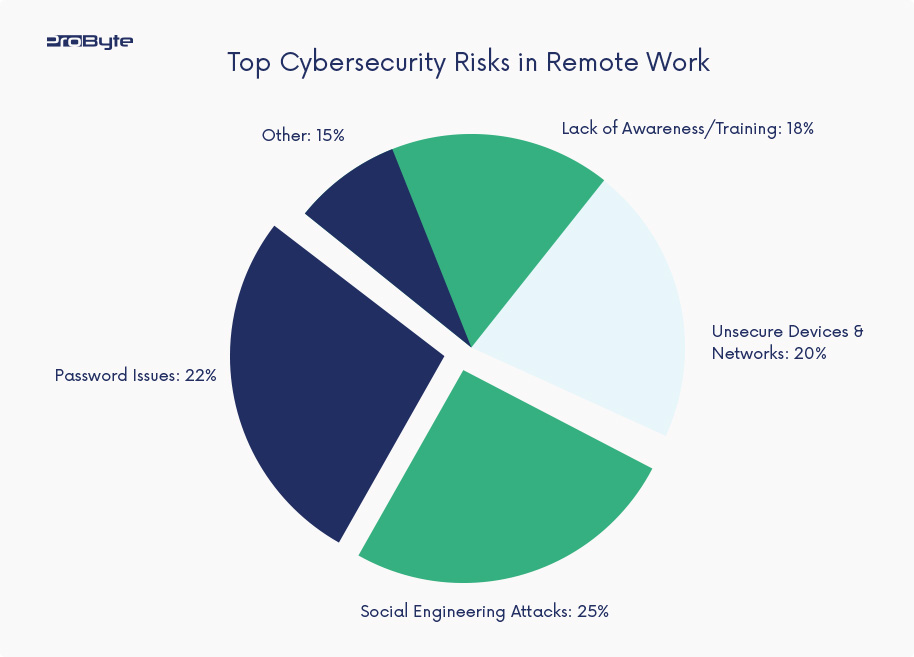 This pie chart highlights the primary cybersecurity concerns that organizations must address in their remote work strategies.
This pie chart highlights the primary cybersecurity concerns that organizations must address in their remote work strategies.
To mitigate the risks associated with remote work, organizations must implement cybersecurity best practices tailored to a distributed workforce.
MFA adds an additional layer of security by requiring users to verify their identity using at least two factors (e.g., a password and a mobile authentication code).
Zero Trust assumes that no one, whether inside or outside the organization, should automatically be trusted. Every access request must be verified before being granted.
Continually educating employees on recognizing phishing attempts, creating strong passwords, and handling sensitive information securely is crucial for maintaining security.
VPNs ensure that all communication between remote workers and company servers is encrypted, reducing the risk of data interception. Encryption should be applied to all sensitive data in transit and at rest.
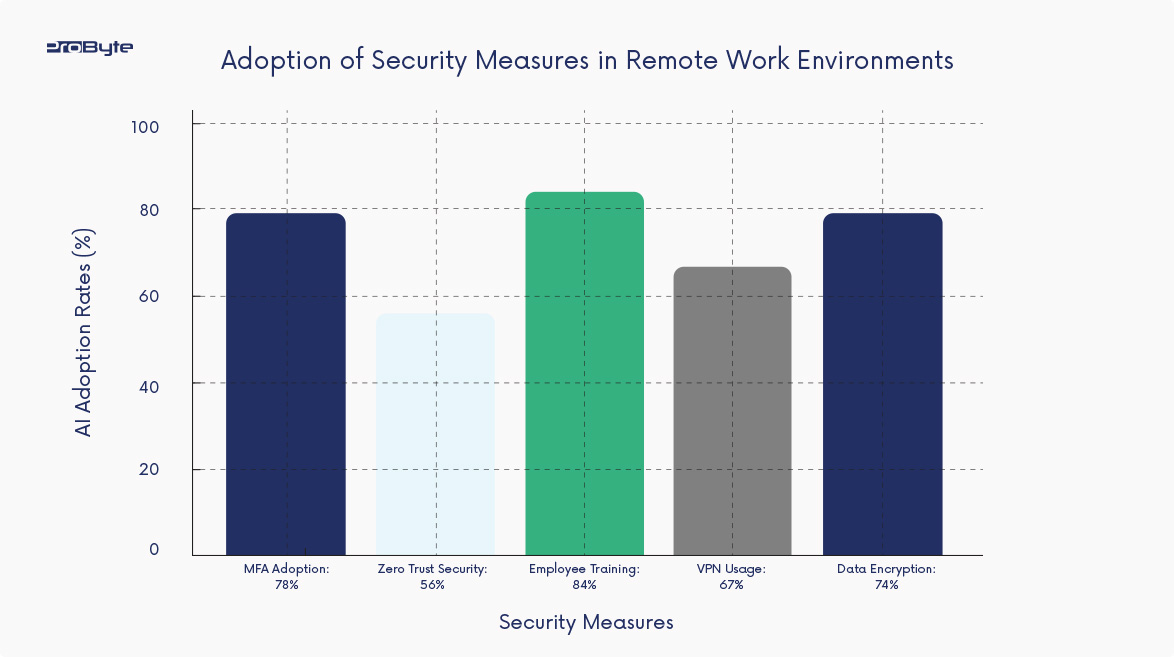 This bar graph shows the adoption rates of key cybersecurity measures across organizations with remote teams.
This bar graph shows the adoption rates of key cybersecurity measures across organizations with remote teams.
Understanding how real businesses have faced cybersecurity challenges while working remotely provides valuable insights. These case studies highlight the vulnerabilities exposed in remote work environments and the lessons learned that can guide other organizations in strengthening their cybersecurity posture.
In July 2020, Twitter experienced a high-profile cyberattack that compromised the accounts of some of its most influential users, including Bill Gates, Elon Musk, and Barack Obama. The attackers gained access to internal Twitter systems through social engineering, targeting employees working remotely and exploiting weak security measures.
The attackers used a technique called SIM swapping, where they gained control of employees' phone numbers by tricking mobile carriers into transferring phone numbers to a device they controlled. Once they had access to Twitter’s internal systems, they used employee credentials to take over accounts and post malicious messages.
The attackers used the hijacked accounts to solicit Bitcoin donations from followers, totaling over $100,000. This breach raised concerns about Twitter’s internal security protocols, especially regarding its remote work practices, and the potential for similar attacks against other companies with remote or distributed teams.
Employee Education:
Remote employees must be continuously trained on recognizing social engineering tactics, particularly those targeting them through their personal devices.
Multi-Factor Authentication (MFA):
Enforcing stronger authentication methods would have prevented unauthorized access to employee accounts, mitigating the impact of the attack.
Access Controls:
Limiting access to critical systems and data to only essential personnel, and implementing more granular control over admin privileges, could have reduced the damage.
The SolarWinds cyberattack, also known as the Sunburst attack, was a sophisticated supply chain attack discovered in December 2020. The attackers, believed to be a state-sponsored group, exploited vulnerabilities in SolarWinds' Orion software, which is used by over 18,000 organizations, including government agencies, Fortune 500 companies, and IT service providers.
The hackers inserted a backdoor into the Orion software updates. When customers unknowingly installed the update, the malware was activated, allowing the attackers to gain access to internal networks. The attack went undetected for several months, with hackers using the access to exfiltrate sensitive data, including emails and internal communications.
The breach affected a wide range of organizations, including U.S. government agencies like the Department of Homeland Security and the Treasury Department. While the full extent of the damage is still being assessed, the incident highlights the risks posed by remote and cloud-based infrastructure, where third-party software plays a central role.
Third-Party Vendor Risk:
Organizations must carefully assess the cybersecurity practices of any third-party vendors, especially when using software or services that are critical to their infrastructure.
Zero Trust Architecture:
The attack demonstrated the need for a Zero Trust security model, where access is continuously verified, and implicit trust is not given to any network or device, even if it’s internal.
Continuous Monitoring:
Implementing continuous monitoring tools, including endpoint detection and response (EDR) software, could have helped identify unusual behavior or suspicious activity earlier in the attack.
In July 2020, Garmin, a global leader in wearable technology, was hit by a ransomware attack that shut down its internal systems and many of its customer-facing services, including its fitness tracking app and website. The attack was attributed to the WastedLocker ransomware group, and it disrupted Garmin's operations for several days.
The attackers exploited vulnerabilities in Garmin's network, encrypting its files and demanding a ransom for their decryption. Since Garmin's operations were largely remote, including its customer support and engineering teams, the disruption caused significant operational challenges. However, the company refused to pay the ransom, and the encrypted data was eventually restored using their own backup systems.
Downtime:
Garmin's website, customer support services, and fitness tracking app were offline for several days, leading to lost business opportunities and frustrated customers.
Financial Losses:
Although the company did not disclose the exact financial impact, it is estimated that the attack cost Garmin millions of dollars in downtime and recovery efforts.
Backup and Recovery Plans:
The incident highlighted the importance of regularly backing up data and having a disaster recovery plan in place to mitigate the damage caused by ransomware attacks.
Employee Access Control:
Limiting access to sensitive systems and using role-based access controls can prevent malware from spreading across the network.
Security Awareness:
Even in a remote work environment, employees must be aware of the risks posed by phishing emails and ransomware. Regular training on recognizing and avoiding suspicious emails could reduce the likelihood of successful attacks.

In the wake of the COVID-19 pandemic, Zoom became the go-to platform for remote communication, with millions of users relying on the platform for business meetings, educational classes, and personal interactions. However, the rapid adoption of Zoom exposed several security vulnerabilities.
The platform faced a series of security issues, including Zoombombing, where unauthorized individuals joined meetings and disrupted them with inappropriate content. Additionally, there were concerns about the platform’s data privacy practices, as some data was being routed through servers in China, raising issues with compliance.
The security vulnerabilities affected organizations worldwide, forcing Zoom to implement several immediate security updates, such as meeting passwords, waiting rooms, and other features to prevent unauthorized access.
Security Patching:
Remote communication tools must be regularly updated to address new vulnerabilities.
User Authentication:
Adding features like meeting passwords and requiring participants to authenticate before joining can help reduce unauthorized access.
Data Privacy Compliance:
Ensure all remote communication tools comply with data privacy regulations, especially if dealing with sensitive customer or employee information.
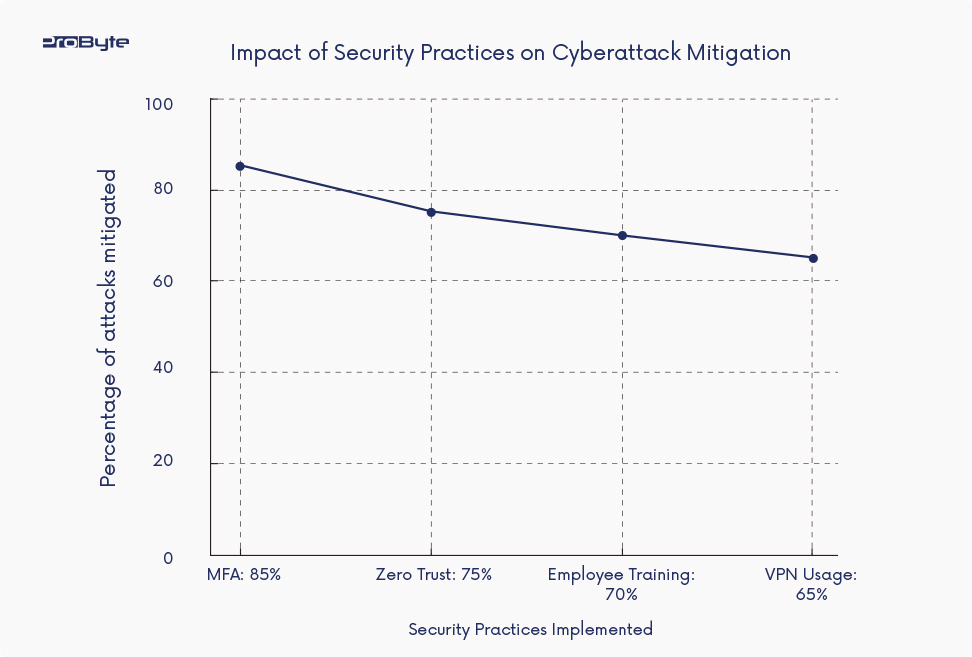 Conclusion
Conclusion
As remote work continues to evolve, organizations must adapt their cybersecurity strategies to address the unique risks and challenges it presents. By implementing best practices, such as MFA, Zero Trust security models, and robust employee training, businesses can significantly reduce their exposure to cyber threats. Case studies from organizations like Twitter, SolarWinds, and Garmin highlight the importance of proactive measures to secure remote workforces and maintain business continuity in the face of evolving cyber threats.